I sometimes come across informative explanations of concepts from other bloggers. Sometimes these explanations are more entertaining than I would ever be able to make them. I sometimes write explanations of concepts here and I try to present them in a way that will make readers interested in reading them. I also sometimes critique explanations that others write. I recently came across “A Stick Figure Guide to the Advanced Encryption Standard (AES)” that explains AES in a way that I thought was both amusing and informative.
This guide to AES, written by Jeff Moser, was presented in a very unique way. It is unlikely that any other guide to AES had ever been written in the form of a series of handwritten illustrations that contain stick figures. However, Mr. Moser wrote a guide to AES that was in this form. This guide consists of four different sections, referred to as the four acts of the story of AES. The first two acts appear to be intended for those who are only interested in understanding what AES is and why it matters. The third and fourth acts cover how AES actually works.
The first act gives a short overview of what led up to the development of AES. While it is intended for those who are not familiar with AES, or cryptography in general, those with some knowledge of cryptography will understand the inside jokes in it. The panel in which ROT13 is mentioned contains a message encrypted with ROT13, followed by a response that says “double ROT13 is better” that might as well have been “encrypted” with two ROT13 rounds. Some will also find it appropriate that when DES is mentioned, it is pointed out that its key length was shortened. It is also appropriate that the attack on DES from Distributed.net is depicted as one that came from many individuals. Triple DES, as well as its performance issues that led to a need for a new data encryption standard are mentioned next. It is then mentioned which algorithms were in competition with each other to become this new standard. The next act consists of a short overview of cryptography.
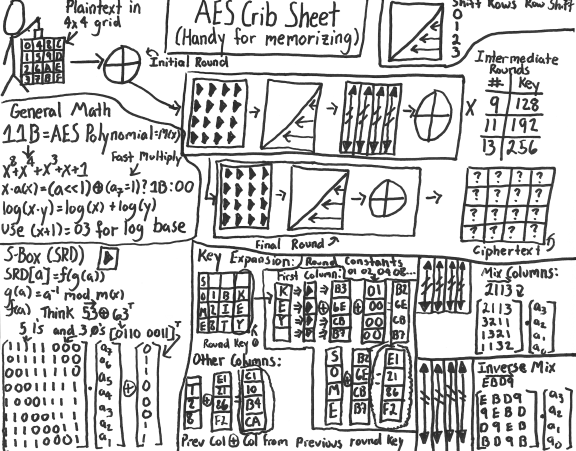
In the third act, the details of how AES works are mentioned. Descriptions of expansion of the key, and the steps commonly referred to as SubBytes, ShiftRows, MixColumns, and AddRoundKey are given. There is not as much humourous material in this section, although some will like how ShiftRows is described in a way that is unlikely to appear in any textbooks that cover AES. There are some details that are not included in this section, such as the details on what S-boxes do, and details on what exactly is done in the MixColumns step. Those details, however, are covered in the next act.
This next and final act covers the mathematics involved in AES in depth. A short review of polynomial equations is given. Shortly after that, some readers may suddenly find the material quite foreign to them. When I read the section on polynomials in finite fields, I needed to have my memory refreshed about concepts that I learned about in a university course on rings and fields years ago. The reason this material is covered gets covered later in the act than some readers might like. How this applies to the mathematics behind S-boxes and MixColumns is covered well, however. Some details are not explained in great detail, such as why certain polynomials are used in certain calculations. Nevertheless, the material is made understandable to those who are willing to take the time to try to “grok” it, as the author says.
Some might be left wondering why certain steps are taken in the AES algorithm. The guide does not give details about how AES is better than DES, and why it might be more resistant to attacks. This absence of explanations of these topics is made into a joke, in which it is suggested that readers would not want to read any further. I was reminded of the statement that Fermat made when he mentioned that he proved his last theorem, and could not fit the proof within the margin of the paper on which that theorem was written. However, more information on AES is available to those who may want to look for it, and this was by far those most amusing explanation of AES that many may ever come across.
While this guide to AES may be considered entertaining, can it also be considered the best guide to AES overall? Some might think that it is, some might not. I personally thought that it helped to see the material presented in this form. If I wanted to learn the details about how AES works, I would have consulted Wikipedia. However, while the Wikipedia article on AES and related ones there are informative, I personally might have been more likely to have my eyes glaze over while reading them. As with any explanation of AES, one might need to re-read sections of the explanation to understand it. However, this guide seems to make going over the material more enjoyable. And while there were previously some inaccuracies in calculations in it, one of which I pointed out, it gave an accurate explanation of how AES works. Links at the end of the guide are provided for those who would prefer more formal explanations of how AES works. AES is complicated, and I consider making explanations of it more entertaining a good idea. For many, it may take time and comic relief to fully understand anything that can be described as follows: